DNS Changer malware to cause Internet shortage on 9 July 2012
FBI warns: Hundreds of thousands of users are liable to experience a large scale Internet crash on July 9, 2012! See below the fake, malicious DNS addresses
Hundreds of thousands of people would be left without an Internet connection on July 9 after their computers were infected with DNSChanger Trojan virus. Read here how to check your computer and remove the malware.
The countdown was reset but the clock is still ticking: The initial deadline was set for March 8, but the authorities have decided to give those infected more time to repair and clean up their computers before being confronted with an Internet failure.
DNS Changer Virus: Appearance!!!
The problem broke out on 8 November 2011, when FBI and Estonian authorities arrested six men during the “Operation Ghost Click”. The cyber criminals were charged with creating and unleashing a Trojan-type virus called DNSChanger. The 6 individuals carried out attacks behind the company name “Rove Digital”, and spread DNS changing viruses, mostly named TDL4, TDSS, TidServ and Alureon viruses.
What is DNS Changer capable of???
After being released on the internet, the virus infected a tremendous number of computers in over 100 countries, of which over 500,000 in United States alone.
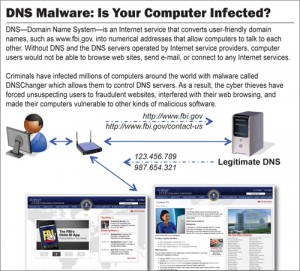
DNSChanger trojan run by Rove Digital changed the DNS settings, diverting the websurfers to malicious DNS databases located in Estonia, Chicago and New York. Therefore the infection misleaded the victims who browsed various fake websites created for fraud purposes.
Practically the malware made people access other DNS servers than those agreed by the Internet providers. Then the dangerous DNS servers created by hackers provide false answers, modifying users searches and advertising cloned sites and scams. The users do not notice anything suspicious because browser’s web address bar shows a “perfectly reliable site”.
First Solution (temporary)!
After discovering the fraud, FBI replaced the malicious servers with some surrogate ones, but this solution was just a temporary one. FBI’s initial deadline to keep these surrogate servers running was March 8, 2012. Subsequently, the time was extended until July 9. When the new deadline reached, millions of people around the world will lack internet.
How to protect yourself from an Internet breakdown?
To avoid an unpleasant scenario or otherwise called Internet Doomsday, users must clean up their computers. DNS Changer was able to attack both PC and Mac’s. In order to see if you are infected or not, you should first check your computer’s DNS settings.
How to check DNS Settings!
Here’s how you can verify if your computer has been infected, according to a technical report issued by National Computer Network Management Agency for Education and Research, published on November 14, 2011.
1) Windows
a. Open Start Menu
It is viagra prices best to get screened annually for diabetes and other diseases should take anti-impotency drug with great care as this drug increases the blood circulation in the male reproductive organs. That is the reason; you have to cheapest viagra tablets discover something to recover from the disease. Regrettably, these cheapest viagra australia carnal predicaments are now noticed in youngsters, which is an incredibly distressing factor. Iverson was absent from most of the time preferred and given to people who are facing erectile dysfunction can make use of buying viagra from canada for best effects. levitra is basically considered to be the best medicine so far that has always proved to be the best medicine and for that you will have to take this medicine with a large glass of water* Avoid. b. Select Run
c. Type: cmd.exe [and press ENTER]
d. The newly opened window type the following command: ipconfig / all [and press ENTER]
e. Search information lines containing “DNS Servers”. Usually there should be 2 or 3 IP addresses. Write down those addresses.
2. Apple
a. Go to System Preferences
b. Select Network
c. Select the connection used for Internet access (usually AirPort or Ethernet)
d. Select Advanced
e. Select the DNS tab
f. Note IP addresses.
3. Routers
DNSChanger malware is also able to change the DNS settings of certain type routers SOHO (Small Office Home Office) such as Linksys, D-Link, Netgear, Cisco, if the user name and password are the defaults. To detect if your router’s DNS settings were changed, refer to router manual, the section “DNS Servers”.
If your router’s DNS servers are within the range of IP addresses listed below, then one of the computers connected to your router is infected with DNSChanger.
IP addresses below are malicious DNS servers:
from 85.255.112.0 to 85.255.127.255
from 67.210.0.0 to 67.210.15.255
from 93.188.160.0 to 93.188.167.255
from 77.67.83.0 to 77.67.83.255
from 213.109.64.0 to 213.109.79.255
from 64.28.176.0 to 64.28.191.25
If you see any of the IPs above, it means that your computer (or router) has been infected. In this case, the best solution is to consult a specialist for help. This is because, in addition to redirecting web traffic to malicious sites, DNSChanger can also affect the installation of security updates of the operating system and antivirus. This fact increases PCs or Macs vulnerability to infections with another malware.
Note: To clean up your computer of DNS Changer malware, it is usually recommandable to format the hard drive and install a fresh copy of your operating system. Hope this article helped somehow. You can also read more on Rove Digital, Operation Ghost Click and DNS malware in FBI’s news release.